✨ Introduction
It starts with an innocuous-looking email. The sender claims to be AWS Support, warning the recipient about an urgent security issue. A single button labeled “Launch Stack” is prominently placed, urging immediate action. What appears to be a standard security advisory is, in reality, the gateway to a sophisticated AWS account takeover attempt.
Threat actors are exploiting AWS CloudFormation StackSets in phishing campaigns designed to compromise AWS environments. Originally reported by Rami McCarthy back in 2022 and by Scott Piper in this blogpost (2021), this technique continues to evolve, demonstrating how adversaries leverage AWS automation against its own users.
🧠 The Anatomy of the Attack
This attack unfolds in a carefully orchestrated sequence:
1. Phishing Bait
The victim receives an email impersonating AWS Support, claiming a critical issue requires immediate remediation. To enhance credibility, the email mimics AWS branding, formatting, and includes a well-known “Launch Stack” button.
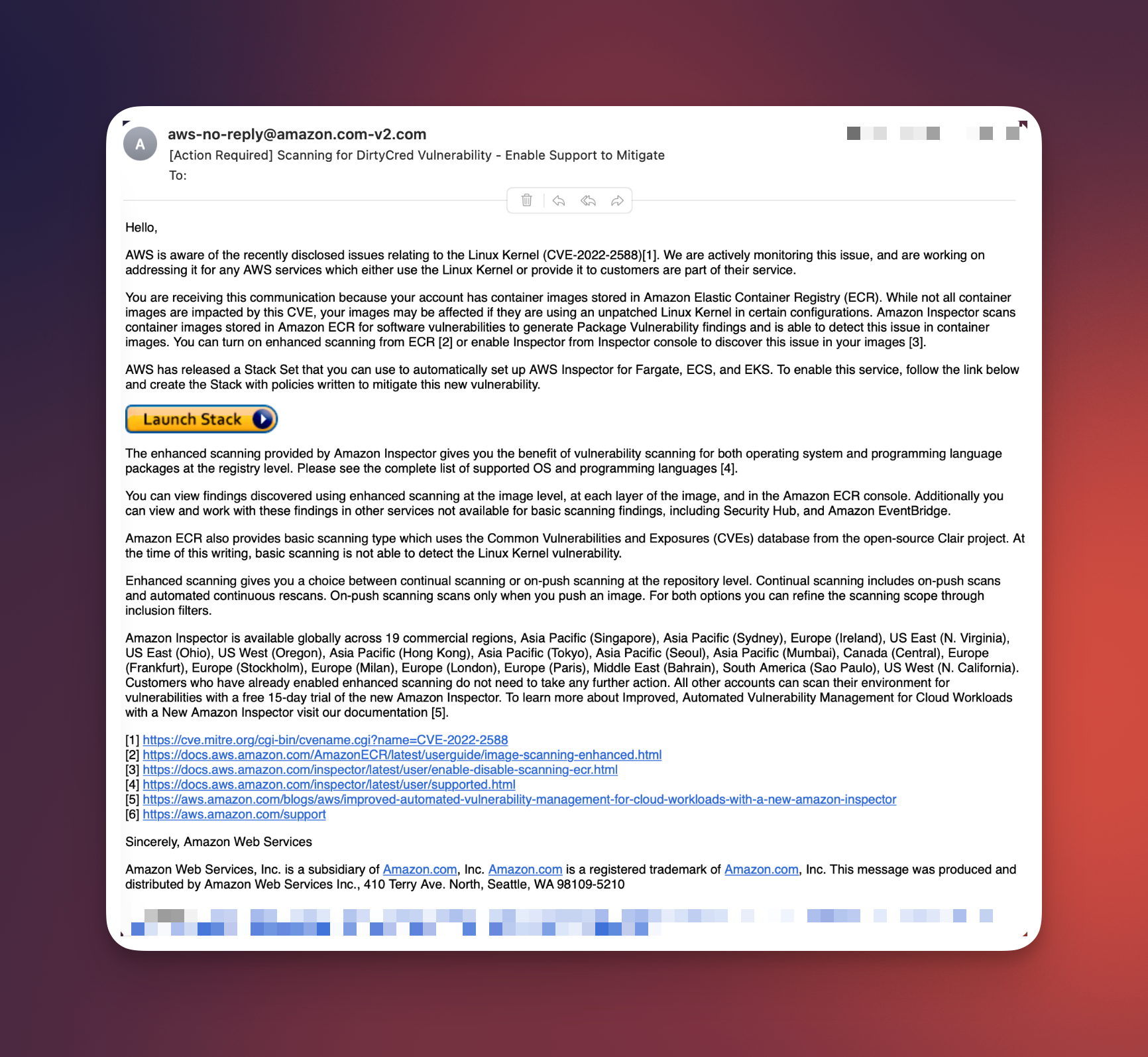
2. CloudFormation Deployment
Clicking the button redirects the victim to the AWS CloudFormation console, where a pre-configured stack is ready for deployment. Unknowingly, the victim launches a CloudFormation template that grants administrative IAM privileges within their AWS account.
3. IAM Role Exploitation
The newly created IAM role includes a trust policy that allows an external AWS account—controlled by the attacker—to assume the role. This grants the adversary direct access without needing credential theft.
4. Exfiltration
Once the role is established, its IAM Role ARN is sent to an API Gateway endpoint controlled by the attacker, enabling them to track compromised accounts and prepare for further exploitation.
5. Account Compromise
With administrative privileges, the attacker can pivot deeper into the AWS environment—creating new IAM users, launching resources, or exfiltrating sensitive data—all while covering their tracks to avoid detection.
🔄 Responding to the Threat
If you discover an unauthorized IAM role in your AWS environment, immediate action is required:
- Remove the CloudFormation Stack – Delete the stack or manually remove the IAM role and attached policies.
- Analyze IAM Role Activity – Use AWS CloudTrail to investigate actions performed by the compromised role.
- Report the Incident – Notify AWS Security at aws-security@amazon.com to escalate the issue.
📘 Proactive Defense Measures (Blue Team)
Prevention is the best defense. Security teams should implement the following controls:
- Tighten IAM Policies – Restrict IAM trust relationships to known AWS accounts and enforce least privilege.
- Use AWS IAM Access Analyzer – Identify and mitigate trust relationships extending beyond your organization’s trusted zones.
- Check External AWS Accounts – Leverage open-source initiatives to identify well-known AWS account IDs associated with malicious activity.
🕵🏼♀️ Advanced Detection Strategies
Security teams can enhance detection efforts using:
- Cloud Security Posture Management (CSPM) Solutions – Commercial platforms like Prowler or Wiz can detect misconfigurations and unauthorized IAM roles.
- (Self-promotion) Open Source Security Tooling – “AWS Security Survival Kit” provides minimal AWS security alerting, covering critical actions used in these attacks (e.g.,
AttachRolePolicy,CreateRole).
📕 Forensics & Threat Disruption
Once an attack is identified, further analysis and countermeasures can help mitigate the impact:
- Identify Malicious AWS Accounts – Review IAM trust policies for external AWS accounts involved in the attack.
- Investigate Attacker Infrastructure – Identify the S3 bucket name used in the Launch Stack URL — this belongs to the attacker.
- Analyze Phishing Domains – Use tools like
urlscan.ioor passive DNS lookups to track attack infrastructure. - Disrupt the Attacker’s API Gateway – Some security teams have experimented with flooding the attacker’s API endpoint with dummy requests to disrupt their operations.
📌 Conclusion
This attack highlights the persistent threats targeting AWS environments. Proactive monitoring, strict IAM policies, and user awareness remain key defenses. By sharing threat intelligence and adopting robust security practices, we can strengthen cloud security and stay ahead of evolving threats.
That’s all, folks! 👋🏼
zoph.