📜 The Origins
Back in 2019, Scott Piper started a Github repository to track changes to AWS Managed Policies. It was a simple setup, manually triggered but it worked well and was incredibly useful. Using git diff or Github.com UI, Scott and the community could easily see how policies evolved over time.
At that time, AWS didn’t publicly share the changes made to managed policies by the various “two-pizza” product teams inside AWS.
Note: If your production workloads depend on AWS-managed IAM policies, you’re adding an external dependency you don’t control. That’s risky and generally not a recommended architecture pattern. What happens if AWS removes a permission or worse, retires a policy?
A safer approach is to copy the content of an AWS-managed policy into your own IAM policy and manage it yourself, on your own timeline.
🤖 From Manual to Automated
After chatting with Scott, I created a fork of his repository with a GitHub Actions workflow and a Fargate task to run the comparison automatically every 4 hours during weekdays. Only changed policies are committed. That’s how the MAMIP project (Managed AWS Managed IAM Policies) was born. Fully automated and running 24/7.
The best part: automation came with notification channels: a Twitter Bot (X) with 2,800+ followers, a Bluesky account, GitHub notifications, and an SNS Topic. The goal was simple: bring AWS policy change visibility to the cloud security community, without anyone having to check GitHub manually.
Over time, I added a few tools that leverage AWS Access Analyzer to detect potential security issues within AWS-managed IAM policies.
🌐 The Companion Website
And today, there’s a Companion website for MAMIP: a clean, searchable archive of AWS-managed policies, complete with a dashboard to explore recent changes.
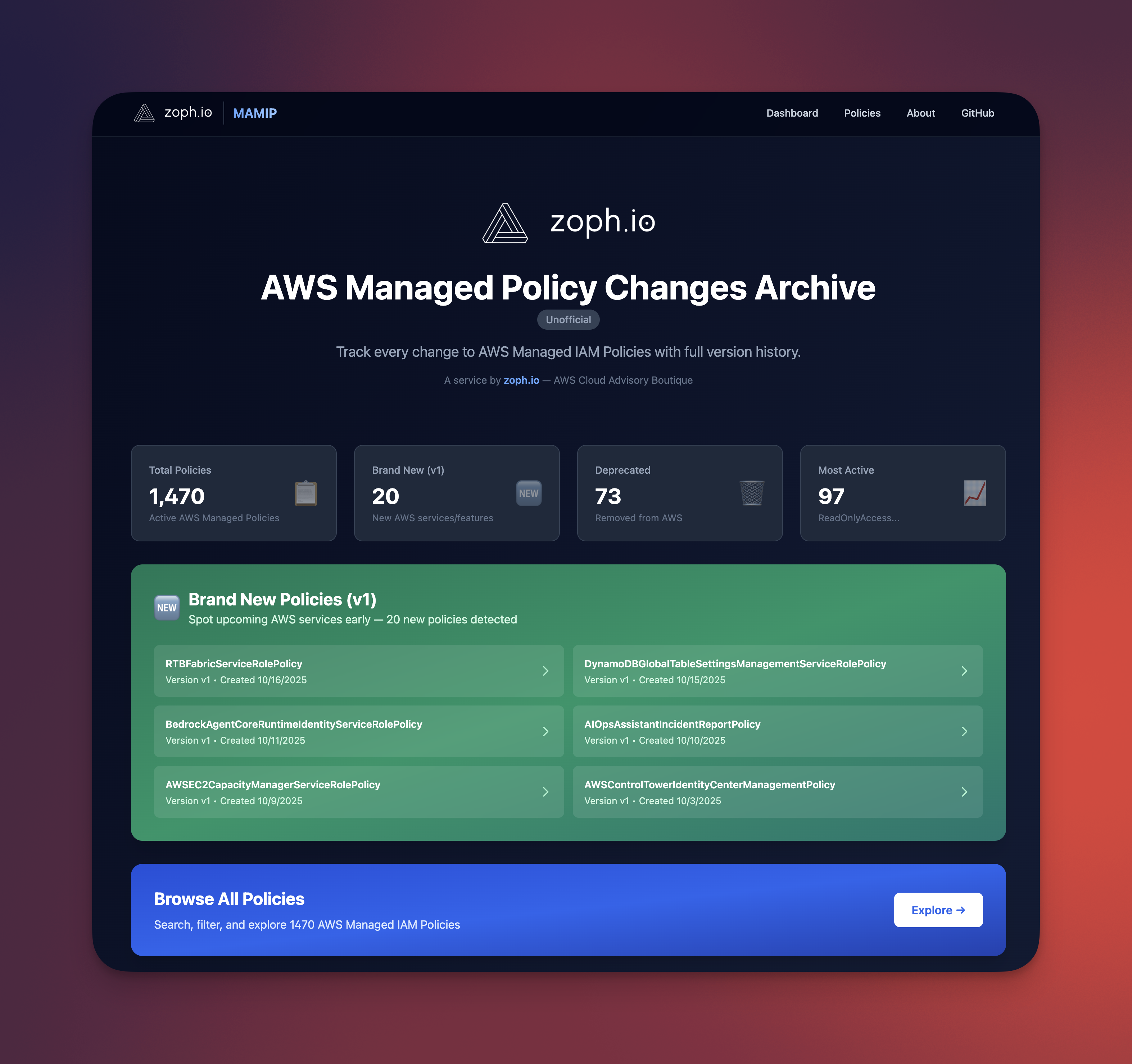
One of the dashboard cards highlights newly created policies (PolicyVersion = v1). A great way to spot new AWS services or features as they launch. (Spoiler alert!)
📌 Conclusion
The MAMIP project continues to evolve, providing the cloud security community with real-time visibility into AWS-managed IAM policy changes. Whether you’re tracking security updates, discovering new AWS features, or ensuring your infrastructure stays current, MAMIP is here to help.
Check out the MAMIP Companion Website and join the community tracking AWS IAM policy changes!
That’s all, folks! 👋🏼
zoph.