This Article was created posted in September 2019. Updated in February 2020.
Disclaimer
Thanks to @0xdabbad00 from SummitRoute for the original idea and
jqparsing.
Purpose
When your production workloads rely on AWS IAM Managed Policies (don’t do this), you will need to be notified when changes occur behind the scene. It’s also interesting to monitor new AWS services releases prior announcements to get spoiled.
This pet project automates the retrieval (every 4 hours) of new AWS Managed IAM Policies to make it easier to monitor and get alerted when changes occur (by AWS) using “Watch” feature from Github, RSS or dedicated Twitter Account.
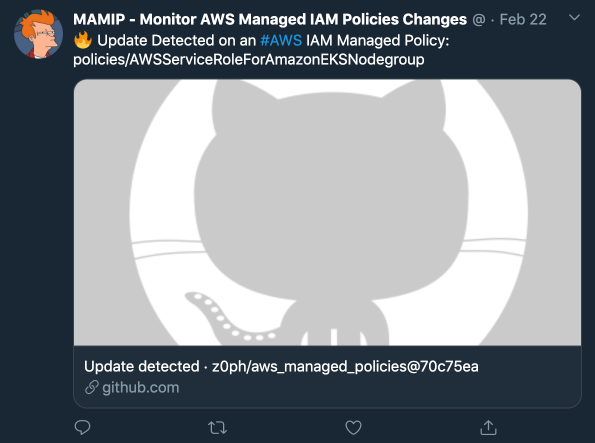
Link: MAMIP - Monitor AWS Managed IAM Policies
Usage
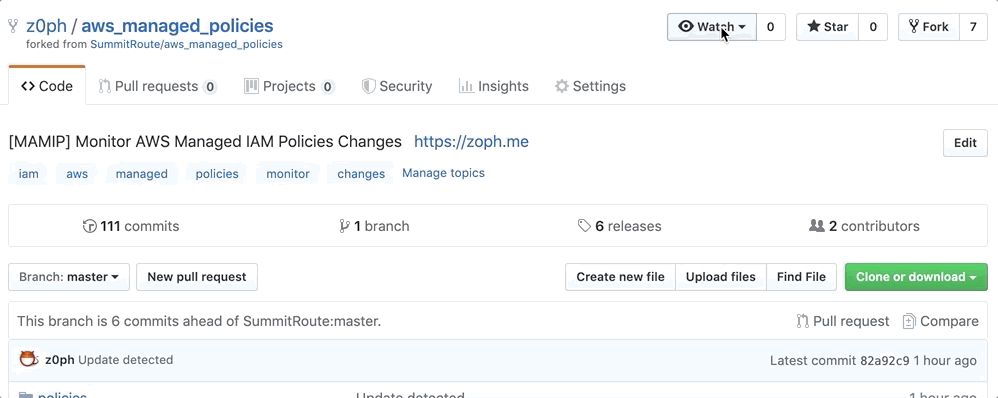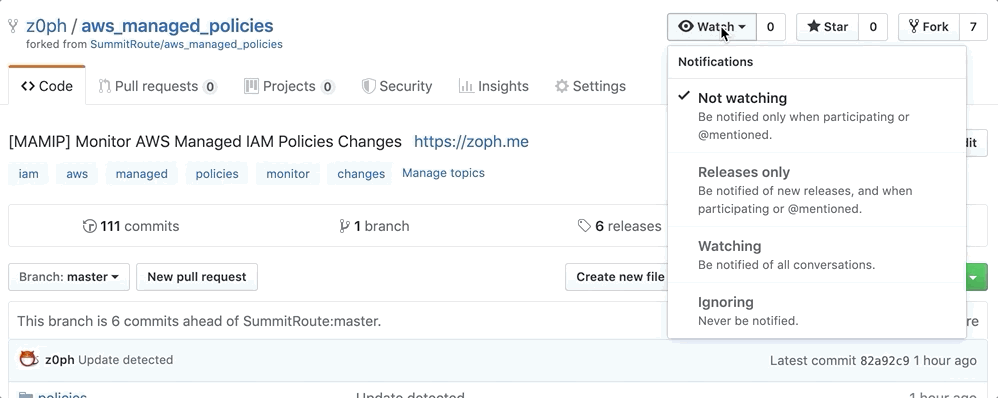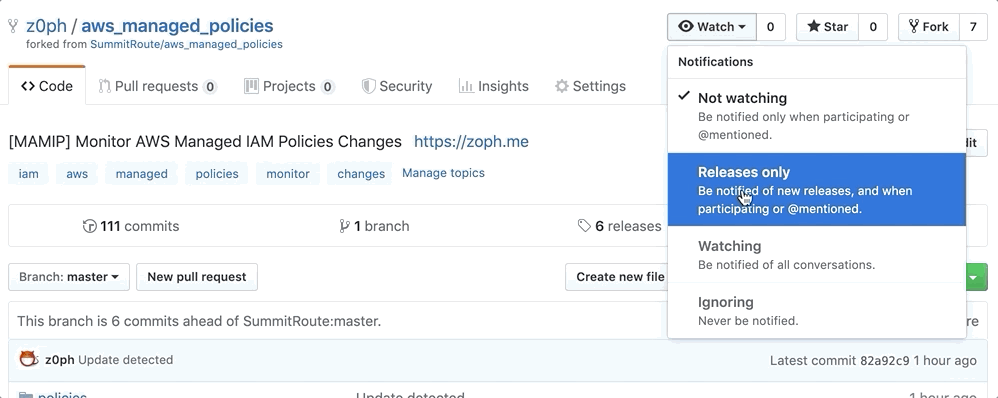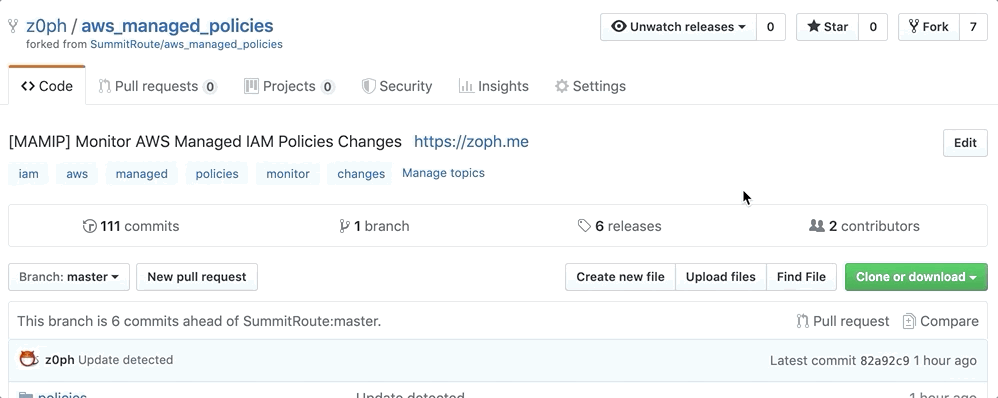
Three options
- Activate
Releases Onlynotifications of Github
- Subscribe to the Github RSS Feed (master branch)
How it works behind the scene
Schema
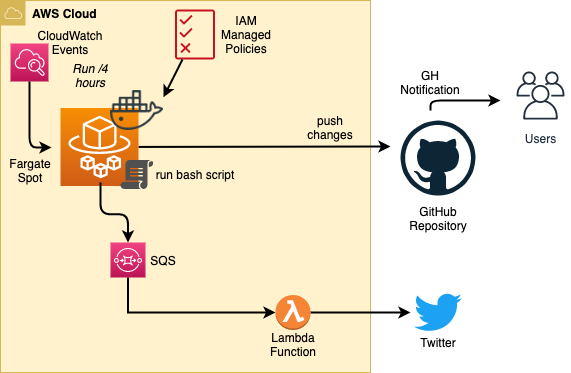
Managed Policies are acquired as follows:
This does the following (the magic):
- Gets the list of all policies in the AWS Account
- Finds the ones with an ARN containing
iam::aws, so that only the AWS managed policies are grabbed. - Gets the ARN, current version id, and policy name (needed so we don’t have a slash as the ARN does for writing a file)
- Calls
aws iam get-policy-versionwith those values, and writes the output to a file using the policy name.
Automation Steps
- Clone the mamip repository
- Run the magic (previous command)
- Commit changes if any
- Push (with tags for release) to Github
- Send message to a SQS queue (qTweet)
- A Lambda function is triggered on SQS message, then push message to Twitter
Schedule
- Every 4 hours
That’s all folks!
zoph.