TL;DR: AWS Managed Policies are safe. Currently.
:arrows_counterclockwise: Previously in Policy Validation
Before AWS Access Analyzer (AA) - Policy Validation release, few open source initiatives were available to lint AWS IAM Policies, like Parliament from Duolabs, CloudSplaining (Salesforce).
The tricky part of these tools is that they are community-driven, from volunteer contributors, and most of the master data comes from AWS IAM docs web scrapping. It is difficult to maintain over time, especially if the documentation format is changing, or if the documentation is not in sync with the IAM reality. It will be easier for everyone if the one who is providing the rules is the one who creates the validation tool to run against these rules — Isn’t it?
:video_game: Why AA - Policy Validation is a game-changer?
The release of AA - Policy Validation is a game-changer because of the direct integration with AWS Console, in the IAM policy editor screen, for IAM Policies only at the moment, but they will bring the same for resource policies like bucket policy or Service Control Policies (SCP) in the next upcoming months.
With this release, AWS publishes 107 checks with different severity levels: error, warning, security_warning, or suggestion. This will help a lot of folks here to review existing policies deployed using Infrastructure as Code, or AWS newcomers who are using console-driven deployments. Even better you will be able to integrate more controls and validation in your automated deployment pipelines.
:champagne: Drink your own champagne
As Brigid said in her own tweet, AWS is drinking their own champagne (or Eat their own dog food :dog:). They’ve updated their procedures to validate their own IAM policies, even if there are still some findings (some are false-positive and are well-documented, to be honest.)
Also, in the Jeff Barr release blog post:
“In the Amazon spirit of drinking our own Champagne, we routinely validate the Amazon-managed IAM policies and fine-tune them when appropriate. From time to time we mark existing managed policies as deprecated, issue notifications to our customers via email, and make updated replacements available. To learn more about our process, read Deprecated AWS Managed Policies.”
:mag: Findings
Following this release I wanted to see by myself how it goes with AA Policy Validation against their own AWS Managed Policies which I’m already monitoring any changes with MAMIP to make my own opinion.
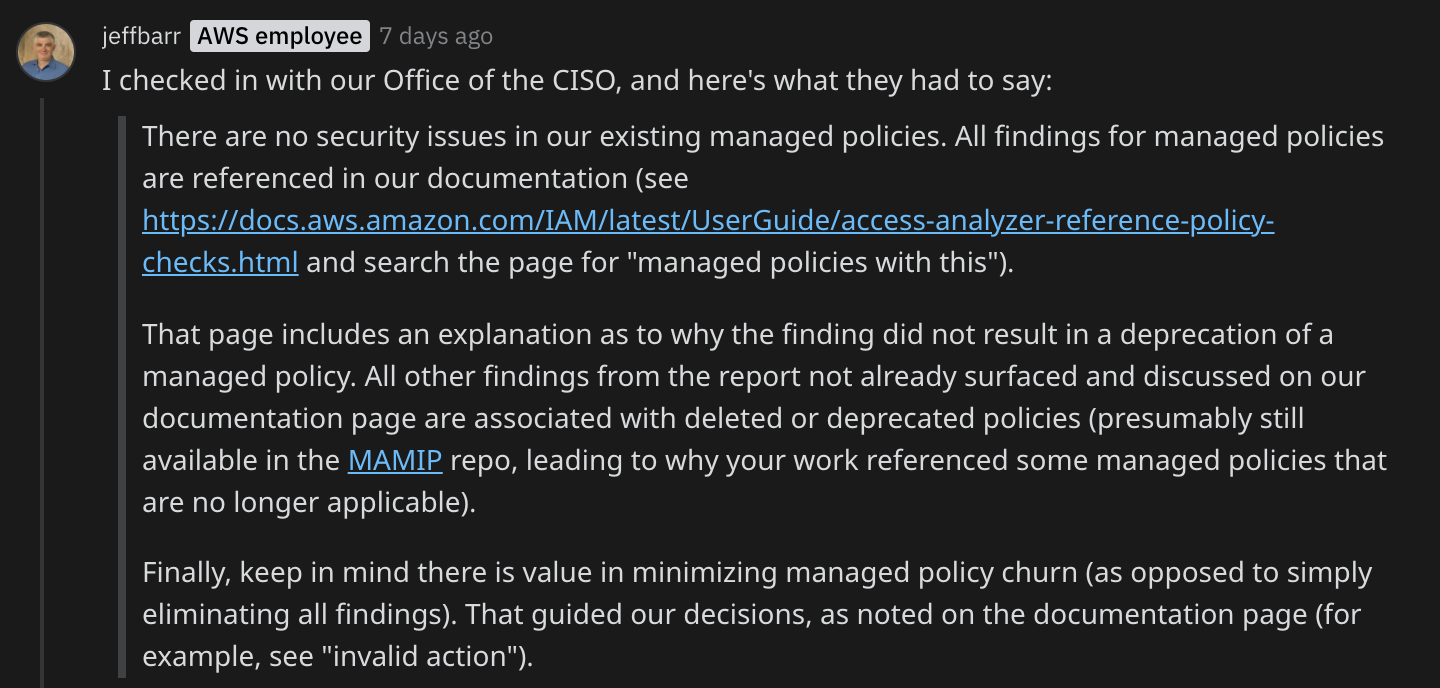
When I’ve published this Twitter thread a few days ago, I’ve tracked a lot of attention from the cloud-sec folks and I’ve got an official answer from AWS teams below:
At that time, the analysis was automated to analyze all 873 policies available on MAMIP repository, even some (35) archived policies that are deprecated now. Take a look some are funny. Give me your preferred one in the comments ;)
You will find up-to-date findings on MAMIP repository. To be fair, I’ve run again my automation to only the current versions of AWS Managed policies.
As the findings are moving fast, here is the commit b4c2f1418 of the analyzed findings. (2021-04-06)
- Policies analyzed:
802 - Errors:
3 - Sec_Warnings:
10 suggestions: 63warnings: 7fail: 1
I will focus my attention on errors and security_warnings only.
Errors
Two errors in this
AWSIoTFleetHubFederationAccesspolicy come from new action not yet known by AA Policy Validation Service.One error in
AWSGlueConsoleSageMakerNotebookFullAccesscomes from a missing qualifier, it’s documented by AWS.
Sec Warnings
Mostly Wildcard (*) in
iam:PassRolepermission, documented. Mostly.
:raised_hand_with_fingers_splayed: Do it for your own customer-managed policies
I’ve created a small python script to analyze all your customer-managed policies (account-wide).
$ python3 -m pip install aa-policy-validator --user
Don’t hesitate to contribute or ask for enhancements!
Conclusion
AWS did a great job by bringing to us new tools with Policy Validation, and more recently a new capability for Access Analyzer to generate least privilege policies based on CloudTrail activity logs. It will help us to apply security best practices and least-privilege approaches with direct integrated tooling. They obviously drank their own champagne, routinely. We hope to see an enhanced AWS Managed Policies shipping quality in the next pushes.
I hope these tools and AWS teams associated will work in sync to avoid false positives and will add more checks in the near future — Like bucket policy and SCP integration and all other policies types.
Remember that this kind of tools was developed by security folks prior AWS, a few years ago: parliament, cloudtracker, cloudsplaining, congrats to many contributors 👏